Demystifying VPNs: A Critical Examination of Their Security Claims
Introduction:
Virtual Private Networks (VPNs) have seen a surge in popularity lately, with promises of heightened online security and anonymity. Nevertheless, it’s important to carefully examine these assertions made by VPN services at a time of increased privacy concerns. Though they do have certain benefits, it’s important to understand that VPNs aren’t always the unbreakable barriers that many think they are. This post seeks to shed light on the inherent drawbacks and possible dangers of using VPN services.
Honeypots and the Anonymity Illusion:
Contrary to popular assumption, not all VPNs provide priority to user privacy. As honeypots, certain VPN service providers could collect and sell user data to unaffiliated parties. Moreover, a lot of VPNs claim to offer total privacy but don’t live up to this claim.
Identity Protection Shortcomings:
VPNs encrypt your internet traffic, but they do not provide complete security from snoopers or identity theft. A VPN cannot protect your identity if you participate in actions that reveal your personal information, such as entering login credentials on websites, choosing weak passwords, or falling for phishing schemes.
Restricted Destination Address Isolation:
VPNs typically lack isolated destination addresses, meaning they offer protection for only a single hop.
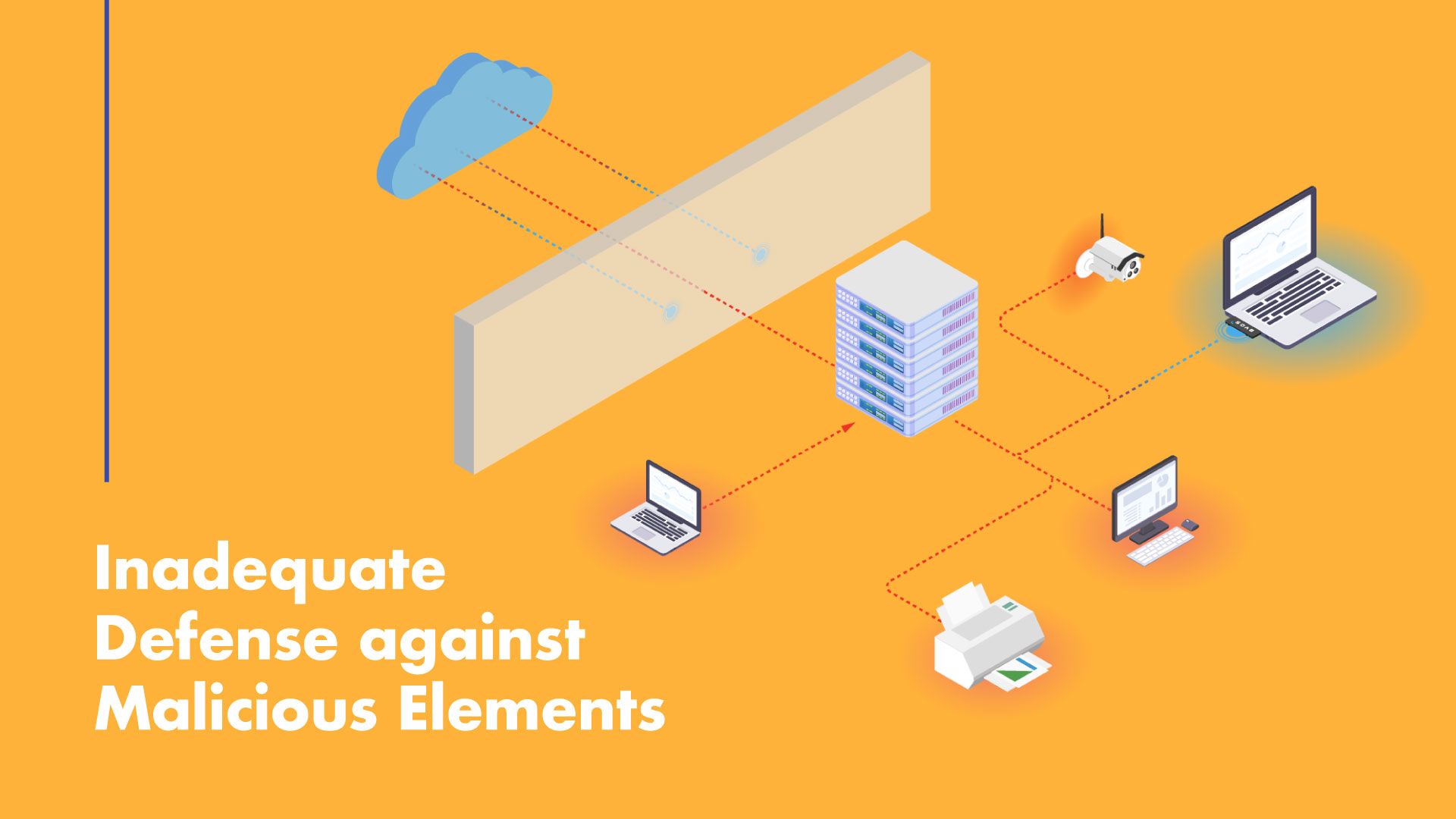
Inadequate Defense against Malicious Elements:
VPNs protect your connection mostly, but they don’t automatically protect you against dangerous connections, files, or malware. It is still possible for these threats to enter your system via social engineering techniques, email attachments, or downloads from unreliable sites.
The Multi-Hopping Mirage:
Some VPN service providers assert that they feature multi-hopping, which means that your data is routed via several servers for increased protection. Your data actually still travels across servers that are either owned or managed by a single provider, even in these circumstances, which raises questions regarding data logging and reliability.
Data Logging and Trust Pitfalls:
Virtual Private Networks often require user data logging for various purposes, like troubleshooting or network performance management. This, however, creates a serious risk because these logs might be legally read by authorities or exploited by hackers. Furthermore, giving up all of your internet privacy and security to a single service provider—as VPNs demand—can lead to deceptive feelings of security.

VPNs vs. Tor:
In contrast to VPNs, Tor (The Onion Router) offers a more complete and decentralized privacy solution. With Tor, it is far more difficult to track down your actions because your data is encrypted and routed across a network of relays run by volunteers. Tor provides more privacy and anonymity than VPNs because of its built-in defense against popular spying methods like traffic analysis.
Tracking Prevention and Dependency on a Single Service:
By hiding your IP address, VPNs can provide some protection from online monitoring; nevertheless, users can still be identified and tracked by other tracking techniques like cookies and browser fingerprinting. Picking a reliable VPN service provider requires careful consideration because putting a lot of faith in one supplier is a big choice.